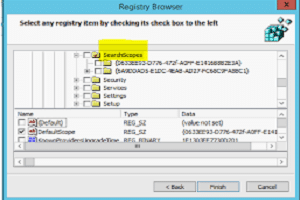
ZHPDiag – Module O83 (SSS)
 Some malware uses the functionality of Svchost to hide from certain diagnostic tools. This is particularly the case with the Conficker worm which has Trojan horse backdoor functionalities.
Some malware uses the functionality of Svchost to hide from certain diagnostic tools. This is particularly the case with the Conficker worm which has Trojan horse backdoor functionalities.
First of all, it attacks system protections by deactivating security software and their updates. It also disables Windows updates. Then he establishes a connection to his server in order to take remote control of the station. Finally it downloads and installs malware programs.
More precisely, the malware service inserts itself as data into the multiple list of the value “NetSvcs” as in the service example “nscpjapu" below :
AeLookupSvc,CertPropSvc,SCPolicySvc,lanmanserver,nscpjapu,gpsvc,IKEEXT,AudioSrv,…
At the same time, the malware service is created in the Services Registry key, and a malware resource is assigned to its “ServiceDll” value, for example:
[HKLM\SYSTEM\CurrentControlSet\Services\nscpjapu\Parameters]
"ServiceDll”=”c:\windows\system32\chfywi.dll"
The Search Svchost Services (SSS) module allows you to list the group of particular services launched by Svchost.exe. These services are installed in the key value data “NetSvcs".
The search is carried out in the Registry key: [HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost].
– Each service of this type is launched through the command “svchost.exe -k netsvcs“. It executes the data of the value “ServiceDll” of the key:
[HKLM\SYSTEM\CurrentControlSet\Services\{NameService}\Parameters]
The role of Trojan horse (Trojan) is to get this parasite onto the computer and install it there without the user's knowledge. The contained program is called the "payload". It can be any type of parasite: virus, keylogger, spyware. It is this parasite, and it alone, which will execute actions within the victim computer. The Trojan horse is nothing other than the vehicle, the one who does "bring the wolf into the fold". It is not harmful in itself because it does not perform any action other than allowing the installation of the real parasite.
ZHPDiag Overview
—\\ Searching for services started by Svchost (SSS) (O83)
O83 – Search Svchost Services: AeLookupSvc (AeLookupSvc). (.Microsoft Corporation – Application Experience Service.) — C:\Windows\System32\aelupsvc.dll
O83 – Search Svchost Services: lanmanserver (lanmanserver). (.Microsoft Corporation – Server service DLL.) — C:\Windows\system32\srvsvc.dll
O83 – Search Svchost Services: gpsvc (gpsvc) . (.Microsoft Corporation – Group Policy Client.) — C:\Windows\System32\gpsvc.dll
—\\ Searching for services started by Svchost (SSS) (O83)
O83 – Search Svchost Services: AeLookupSvc (AeLookupSvc). (.Microsoft Corporation – Application Experience Service.) — C:\Windows\System32\aelupsvc.dll [62464]
O83 – Search Svchost Services: lanmanserver (lanmanserver). (.Microsoft Corporation – Server service DLL.) — C:\Windows\system32\srvsvc.dll [168448]
O83 – Search Svchost Services: gpsvc (gpsvc) . (.Microsoft Corporation – Group Policy Client.) — C:\Windows\System32\gpsvc.dll [591360]
Example of detection
—\\ Searching for services started by Svchost (SSS) (O83) (Unsigned cases)
O83 – Search Svchost Services: TrkServer (TrkServer). (…) — C:\Windows\system32\chfywi.dll [14336] =>Trojan.Conficker
O83 – Search Svchost Services: SSHNAS (SSHNAS) . (…) — C:\WINDOWS\system32\sshnas21.dll [0] =>Trojan.Downloader
O83 – Search Svchost Services: fxuuamsy (fxuuamsy) . (…) — c:\windows\system32\uhxhdjn.dll [0] =>Trojan.Downloader
O83 – Search Svchost Services: kdjqggia (kdjqggia) . (…) — C:\WINDOWS\system32\bwuppbn.dll [0] =>Trojan.Vundo
O83 – Search Svchost Services: ygwhngul (ygwhngul) . (…) — C:\WINDOWS\system32\dteekyl.dll [0] =>Trojan.BHO.H
—\\ Searching for services started by Svchost (SSS) (O83) (Signed cases)
O83 – Search Svchost Services: SSHNAS (SSHNAS) . (.ApexDC++ Development Tea – Ape.) — C:\WINDOWS\system32\sshnas21.dll [247808] =>Trojan.Downloader
—\\ Searching for services started by Svchost (SSS) (O83) (Cases signed with usurpation of the name of the legitimate owner)
O83 – Search Svchost Services: SSHNAS (SSHNAS) . (.Electronic Arts – Command And Conquer Generals World Builder.) — C:\WINDOWS\system32\sshnas21.dll [242176] =>Trojan.Downloader
O83 – Search Svchost Services: nmkjifcz (nmkjifcz) . (.Microsoft Corporation – WPD Tracing.) — c:\windows\system32\wdaqqaa.dll [88576] =>Trojan.Conficker
ZHPFix action
O83 – Search Svchost Services: {NameService} ({KeyService}). (…) — {FileName}
{Key}: Registry key [HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost]
{NameService}: Data of the value of “NetSvcs” of the Key {Key}.
{KeyService}: Under key of the key [HKLM\System\CurrentControlSet\Services].
{FileName}: Value data “ServiceDll” of the key [HKLM\System\ControlControlSet\Services\{KeyService}\Parameters].
1) The tool removes the m servicealware {KeyService}.
2) The tool deletes the file {FileName}.
ZHPFix Report (Example)
Line entered:
O83 – Search Svchost Services: SSHNAS (SSHNAS) . (.Electronic Arts – Command And Conquer Generals World Builder.) — C:\WINDOWS\system32\sshnas21.dll [242176]
Report of ZHPFix v1.12.3133 by Nicolas Coolman, Update of 02/08/2010
========== Registry Key(s) ==========
O83 – Search Svchost Services: SSHNAS (SSHNAS) . (.Electronic Arts – Command And Conquer Generals World Builder.) — C:\WINDOWS\system32\sshnas21.dll [242176] => Key removed successfully
========== File(s) ==========
C:\WINDOWS\system32\sshnas21.dll => Deleted and quarantined
========== Summary ==========
1: Registry key(s)
1: File(s)
Links
* How to remove Conficker virus
* Downadup/ Conficker
* How malware hides by installing itself in service (Malekal)

 Some malware uses the functionality of Svchost to hide from certain diagnostic tools. This is particularly the case with the Conficker worm which has Trojan horse backdoor functionalities.
Some malware uses the functionality of Svchost to hide from certain diagnostic tools. This is particularly the case with the Conficker worm which has Trojan horse backdoor functionalities.